From opening bank accounts to accessing government services, the ability to verify one’s identity securely and remotely has transformed modern life. But as technology has advanced, so too have the methods of cybercriminals. Among the most dangerous and difficult-to-detect threats to identity verification is the Man-in-the-Middle (MitM) attack: when a third party secretly intercepts the communication between two entities without their knowledge.
In the context of identity verification, this means an attacker could capture or alter biometric data—such as a selfie or voice recording—while it is being transmitted from the user’s device to the verification server.
According to Veridas, 3% of onboarding attempts across our clients are fraudulent. The average financial loss per fraud event is around €4,000 and can reach up to €11,000 in more complex cases.
This underscores the importance of implementing a robust fraud prevention solution to protect digital identity verification workflows against the entire spectrum of fraud.
The Spectrum of Attacks: Analog and Digital
Veridas classifies biometric fraud techniques into two broad categories: analog attacks and digital attacks, each with specific subtypes that target different stages of the verification process.
Analog Attacks
Analog attacks involve physical or visual deception in front of a camera. They include:
Presentation Attacks
Presentation Attacks refer to intentional attempts to deceive biometric systems by presenting forged or manipulated biometric evidence. These attacks are performed directly in front of a sensor, such as a camera, to trick the system into accepting a false identity.
Common examples include:
- Printed photographs
- Digital screens displaying another person’s face
- High-quality silicone masks or 3D facial reconstructions
How to prevent them: The most effective countermeasure is the implementation of robust liveness detection techniques. These systems are designed to determine whether the biometric data originates from a real, live person, rather than a replica or static image.
Digital Attacks
Injection Attacks occur when attackers insert fake biometric data directly into the verification system, bypassing the camera or microphone. This is done through digital means, making it more difficult to detect with traditional liveness detection.
Common examples include:
- Deepfake videos or pre-recorded clips streamed via virtual webcams
- Emulators or debugging tools used to inject biometric content into the system
How to prevent them: Security teams should analyze user behavior for suspicious patterns and evaluate the software and hardware environment. This includes checking for virtual devices, emulator activity, and inconsistencies in device performance (e.g., unusual camera specifications).
Man-in-the-Middle (MitM) Attacks
This type of attack intercepts biometric data during transmission between the user and the verification server. The attacker positions themselves to capture or modify sensitive data before it reaches its destination.
How to prevent them: Implement end-to-end encryption and watermark the biometric evidence using secure capture SDKs to ensure data integrity and detect tampering.
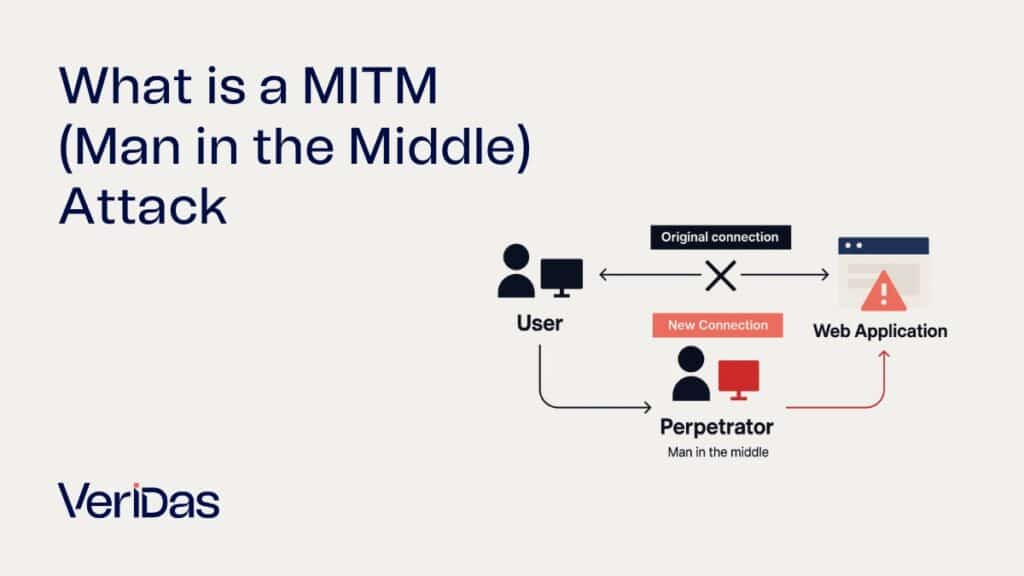
What Is a Man-in-the-Middle Attack?
A Man-in-the-Middle attack occurs when a third party intercepts communication between two systems or individuals, unbeknownst to either of them. In the context of identity verification, this means an attacker could intercept or manipulate biometric data (like a selfie or voice sample) during its transmission between the user’s device and the verification server.
Real-World Risk in Identity Systems
Identity verification systems are especially vulnerable because they often:
- Transmit sensitive personal and biometric data
- Operate over potentially unsecured networks (e.g., public Wi-Fi)
- Use mobile or web-based capture SDKs that could be manipulated in unsafe environments
Common Techniques Used in MitM Attacks
Common techniques used in MitM attacks include:
- HTTPS Spoofing and SSL stripping
- DNS spoofing to redirect traffic to malicious servers
- Session hijacking by stealing authentication tokens
- Rogue Wi-Fi hotspots that mimic legitimate networks
In identity verification, such exploits could allow attackers to alter ID photos, substitute biometric data, or hijack a verification session.
Why MitM Attacks Are Dangerous for Identity Verification
A successful MitM attack on an identity verification process could lead to:
- Full impersonation of a legitimate user
- Unauthorized account access
- Fraudulent onboarding with stolen or synthetic identities
- Reuse or manipulation of biometric evidence
This is especially critical in industries like:
- Banking and fintech (e.g., account creation, transaction approval)
- Telecommunications (e.g., SIM swaps)
- Public administration (e.g., issuance of digital certificates)
Preventing Man-in-the-Middle Attacks: Best Practices
Veridas recommend layered defenses to prevent and detect MitM attacks. Here are essential security strategies tailored for identity verification platforms:
1. Implement End-to-End Encryption and Watermarking
Encrypt all biometric data transmissions using TLS 1.2+ and watermark the captured evidence (e.g., selfie, ID photo) using Veridas’ secure capture SDKs. This ensures that biometric data cannot be intercepted or altered undetected during transmission.
2. Use Secure Capture SDKs
Use certified and tamper-resistant SDKs for identity capture. Veridas SDKs are capable of:
- Real-time glare and angle correction
- Liveness detection at the point of capture
- Detection of virtual cameras or emulators
3. Apply Real-Time Liveness Detection
Ensure that biometric input (selfie or voice) is coming from a real, live user. Veridas is one of the few vendors with iBeta ISO 30107-3 Level 2 certification for both active and passive liveness in web and native environments.
4. Detect Injection and Emulator-Based Attacks
Deploy backend logic to detect when data is injected using developer tools, virtual cameras, or emulated environments. Veridas’ backend services can flag these conditions and block the process immediately.
5. Avoid Public or Unsecured Networks
Educate users not to complete identity verification over public Wi-Fi or unknown networks. Combine with mobile app logic to flag risky environments.
How Veridas Protects Against MitM Attacks
Veridas employs a secure-by-design architecture, with multi-layered protections specifically tailored for identity workflows:
- All identity processing is done in the back-end, avoiding execution on the client side where MitM attacks are easier.
- TLS 1.2+ encryption, IP whitelisting, and API authentication protect data in transit.
- Watermarked biometric evidence ensures data cannot be altered post-capture.
- Injection attack detection blocks attempts to feed manipulated media into the system.
- No data is stored unnecessarily, and biometric vectors are irreversible and non-interoperable.
Final Thoughts: Securing Identity in an Interceptable World
Man-in-the-Middle attacks remain a serious threat in digital identity systems, especially as fraudsters adopt advanced spoofing and interception techniques. Organizations must go beyond traditional HTTPS protections and implement identity-specific defenses like:
- Backend-only processing
- Real-time liveness and fraud detection
- Watermarking of biometric captures
- Secure SDKs with environmental checks
Solutions like those from Veridas are not only compliant with GDPR and the European AI Act, but they also represent a best-in-class defense model based on continuous innovation and trusted certifications.
FAQs: Man-in-the-Middle Attacks in Identity Verification
What is a Man-in-the-Middle attack in identity systems?
It’s an attack where someone intercepts communications between a user and a verification system, potentially altering or stealing biometric or identity data.
What’s the difference between MitM and injection attacks?
MitM involves interception during communication. Injection involves feeding fake data directly into the system, bypassing the camera or microphone.
Can encryption prevent MitM attacks?
Yes, especially when combined with SDK watermarking and liveness detection.
How does Veridas prevent MitM attacks?
Through backend processing, encrypted transmission, biometric watermarking, and emulator/injection detection.
Is Veridas compliant with international regulations?
Yes. Veridas solutions meet GDPR, ISO 27001, iBeta PAD Level 2, and are aligned with the AI Act.