The way we prove and manage who we are online is undergoing a dramatic transformation. Traditional digital identity systems – like using passwords, social logins, or centralized ID databases – are increasingly seen as insecure and inconvenient. It is time for decentralized identity.
Data breaches are on the rise, and 75% of security professionals reported an increase in cyberattacks in 2023, often targeting centralized identity stores. In response, a new approach called decentralized identity (also known as self-sovereign identity) is emerging as the future of digital identity.
This model uses cryptography and often blockchain technology to give individuals greater control over their own personal data. It’s not just a boost to security – it’s a fundamental shift that puts users back in the driver’s seat of their digital lives.
In this article, we’ll break down what decentralized identity is and how it works. We’ll look at how it differs from the traditional identity systems we’re used to, and explore the key components that make it possible – including Decentralized Identifiers (DIDs) and verifiable credentials. We’ll also discuss the role of the Decentralized Identity Foundation (DIF) in shaping this ecosystem.
Finally, we’ll dive into the benefits of decentralized identity (like better privacy, security, and user control) and real-world use cases in finance, healthcare, and beyond, before examining the challenges ahead and why many believe decentralized digital identity is indeed the future of identity management.
What Is Decentralized Identity?
Decentralized identity is a framework for identity management that moves away from centralized authorities and gives individuals control over their own digital identities. In simple terms, it means you manage your identity through credentials you hold, rather than an organization (like a government, bank, or tech company) managing it for you.
Your digital identity is made up of information about you – for example, your name, date of birth, passwords, payment info, diplomas, etc. – and in a decentralized model, this information isn’t all stored in one big database. Instead, it’s distributed and secured by cryptography, often with the help of blockchain or other distributed networks.
In a decentralized identity system, there are typically three key roles: an issuer, a holder, and a verifier. Imagine you have a driver’s license in digital form. The motor vehicle agency (issuer) can issue you a digital credential that says “this person is licensed to drive.”
You, the user (holder), store this credential in a secure digital wallet on your device. When needed, you can present proof of your license to, say, a car rental company (verifier) which then checks the credential’s authenticity.
There’s no central database that the rental company needs to query – instead, they verify the digital signature on your credential to trust it. This is fundamentally different from how identities are handled in centralized systems, and it allows you to control which pieces of your identity to share, with whom, and when, enhancing privacy and security by design.
In essence, decentralized identity lets people prove things about themselves in a trusted way without handing over all their data to centralized intermediaries.
How It Differs from Traditional Identity Systems
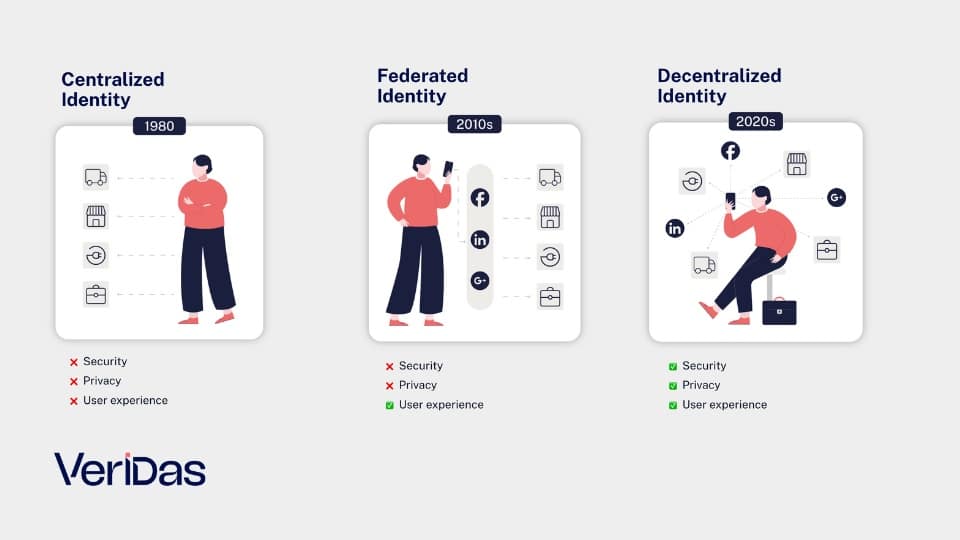
Decentralized identity differs from traditional identity systems in several fundamental ways. In traditional (centralized) identity systems, all your information is stored and managed by a central authority or provider – think of your data sitting in a big database at a government office or on a corporate server.
This creates a single point of failure: if that central database gets hacked or leaks, all user data can be exposed at once. Users also have limited control in such systems; you often have to trust the provider to keep your data safe and use it appropriately, and you usually have to share the same personal details over and over with different services.
For example, when you sign up for a new bank account or a new app, you provide personal information again, and it gets stored in yet another silo beyond your control. In federated identity models (like “Log in with Facebook/Google”), you rely on a big tech company to vouch for you – but that still means handing control of your online identity to a third party.
In decentralized identity systems, there is no single company or government holding all the keys to your digital identity. Your data is spread out and secured with you, the user, in control. Rather than a single database, information is verified using cryptographic proofs and distributed networks, so there’s no central honeypot for hackers to attack. If an attacker wanted to compromise your identity in a decentralized system, they’d have to breach multiple independent systems (and even then, much of the data may not be stored centrally at all), which is far more difficult.
Another big difference is the trust model: in traditional systems, the verifier (like a service you use) has to directly trust the issuer or identity provider and often form a relationship or integration (for example, a partnership between a social login provider and an app). In decentralized identity, trust is unidirectional – a verifier can trust the credential because it’s cryptographically signed by an issuer, without the issuer even needing to know the verifier.
This one-way trust flow, enabled by cryptography, means you don’t need all parties on a shared database or agreement ahead of time. It also enables privacy enhancements like sharing only specific proofs.
For instance, you could prove you are over 18 without revealing your exact birthdate or any other info, by using a credential or zero-knowledge proof that only discloses that one fact. In summary, decentralized ID flips the current script: instead of organizations being the source of identity and users having to conform, the user becomes the center – holding their identity and deciding who gets to see it.
Decentralized Identity Key Components & Management
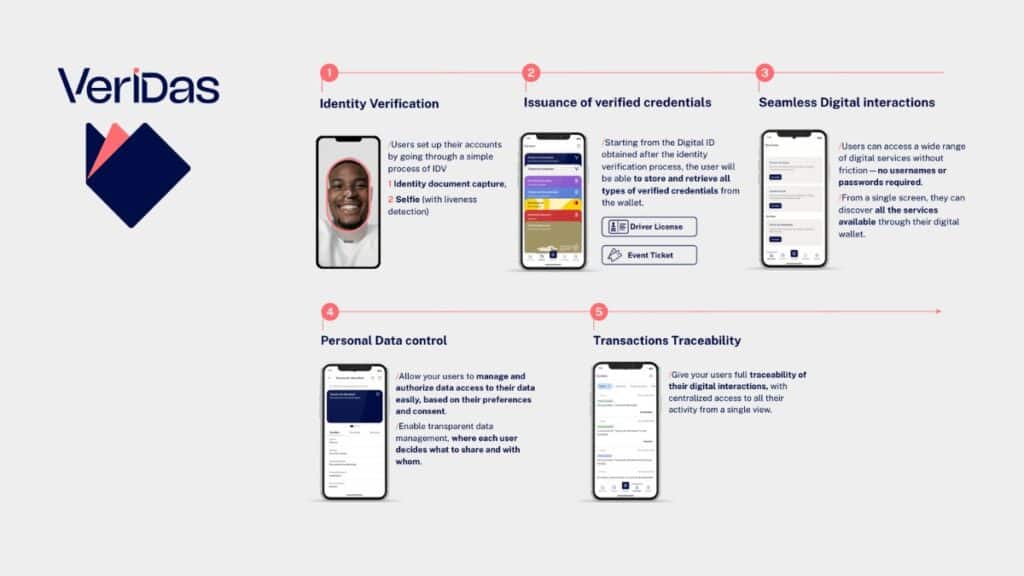
A digital identity wallet app on a smartphone shows multiple credentials (Digital ID, Employee ID, Driver License). Such an ID wallet is a key component of a decentralized identity system, allowing users to store and manage their decentralized ID credentials securely on their own device.
To make decentralized identity work, a few core components and concepts come together. These include Decentralized Identifiers (DIDs) as the new kind of identifier for entities, Verifiable Credentials (VCs) as the digital attestations or ID documents, and infrastructure or standards organizations like the Decentralized Identity Foundation (DIF) that ensure everything works together.
These pieces collectively enable what we call decentralized identity management, where the user manages their identity through technology (often an app or wallet) rather than a central provider managing it for them. Let’s look at each component and how they function in a decentralized identity system.
Decentralized Identifiers (DIDs)
A Decentralized Identifier (DID) is basically a new type of unique identifier that isn’t issued by any central authority – instead, it’s registered in a decentralized way (for example, on a blockchain or distributed ledger).
You can think of a DID like a username or address that you fully own and control, analogous to how you might control a domain name, except it’s for your identity. A typical DID might look like did:example:123456abcdef... rather than a familiar format like an email.
What makes DIDs special is that they are globally unique, persistent, and tied to cryptographic keys that you control. When you create a DID, you also generate a pair of keys: a private key (which you keep secret) and a public key. The public key, along with other information (like ways to contact you or verify data), is published in a DID Document that is accessible on the network.
Because you have the private key, you can prove that the DID is “yours” by signing messages. No central registry (like a government ID database or a certificate authority) is needed to vouch for that link – the proof comes from possession of the cryptographic key.
The significance of DIDs is huge for decentralized identity. They provide a foundation of trust without centralized control. For example, if Alice has a DID and Bob has a DID, Alice can digitally sign a credential for Bob (like a certificate or ID card) and Bob can present it to Carol; Carol can then use Bob’s DID and Alice’s DID (and their associated public keys) to verify that the credential is legitimate and was issued by Alice.
This can all happen without any of them having to query a central server or ask permission from an outside authority. Each DID is like a self-contained trust anchor. Many DIDs are anchored on blockchains or similar networks to make them tamper-resistant and globally resolvable, but it’s not strictly required that they use blockchain – the key idea is decentralization.
The World Wide Web Consortium (W3C) has even standardized DIDs to ensure they work universally. In practice, when you use a decentralized identity wallet, it will create and manage DIDs for you behind the scenes. For instance, you might have a DID for yourself that your wallet uses when interacting with various services.
Because you can have many DIDs (even one per relationship or service), it also helps prevent correlation – each service sees a different identifier for you, making it harder to track you across contexts. In short, DIDs replace the need for usernames or IDs issued by someone else; they let you establish your digital identity on your own terms, backed by strong cryptography.
Verifiable Credentials
If DIDs are like your identity’s address or account, verifiable credentials (VCs) are like the contents of your identity – the digital equivalent of the cards and documents in your physical wallet. A verifiable credential is a tamper-proof digital credential that contains claims about you (or an entity), issued by some authority, and cryptographically signed so it can be independently verified.
Think of a verifiable credential as a digital version of a driver’s license, passport, diploma, employee ID, vaccine certificate, or even a library card – any credential you have in the real world can be its digital verifiable counterpart. What makes it “verifiable” is that anyone who needs to check it can do so using the issuer’s public key (often via the issuer’s DID).
If even one bit of the credential was altered, the signature check would fail, so it’s tamper-evident and trustworthy. The credential typically includes the subject’s DID (who it’s about), the issuer’s DID (who issued it), the claims (e.g., “birthdate is 1990-01-01” or “has driving privilege”), and an expiration date or other metadata, all signed by the issuer.
Verifiable credentials are central to decentralized identity management because they carry the actual information that gets shared. How they are managed is usually via a digital wallet or app that stores your credentials securely (often encrypted) on your device.
For example, you might have a “Digital ID” credential issued by a government, a “Employee ID” issued by your company, and a “Bank KYC Verified” credential from a bank after you complete a one-time verification. These credentials live in your ID wallet, and you decide when to present them. When a verifier (like a service or another person) requests proof, you can share a verifiable presentation – essentially a package of one or more credentials or even a derived proof from them, tailored to that request. Importantly, you might not need to share the entire credential; you could share just certain attributes.
For instance, if a bar needs to verify you are over 18, your wallet could create a presentation from your driver’s license credential that only confirms you’re over 18, without revealing your exact birth date or address. Techniques like this (often using zero-knowledge proofs or selective disclosure) ensure privacy while still proving the necessary information.
The benefit for businesses and verifiers is significant: they can instantly trust the information presented without having to contact the original issuer each time.
For example, an employer can verify a candidate’s digital diploma credential in seconds rather than waiting days for a university to respond, since the credential is digitally signed and fraud-proof. Overall, verifiable credentials enable secure, efficient, and user-centric sharing of identity information, forming the backbone of a decentralized identity system’s functionality.
Role of the Decentralized Identity Foundation (DIF)
Building a decentralized identity ecosystem requires many players (tech companies, standards bodies, governments, etc.) to agree on how things work and to ensure different systems can talk to each other.
The Decentralized Identity Foundation (DIF) plays a pivotal role in this. The DIF is an engineering-driven organization focused on developing the foundational elements necessary to establish an open ecosystem for decentralized identity and ensure interoperability between all participants.
In other words, DIF is like a collaboration hub where experts and organizations come together to make decentralized identity technology practical on a global scale. Founded by a group of industry leaders, DIF’s members include tech companies, startups, non-profits, and even government bodies, all working on identity solutions.
They collaborate on open standards, protocols, and tools so that (for example) a credential issued in one system can be recognized in another, or a DID created on one platform can be resolved by another platform. This avoids the emergence of isolated “identity silos” and instead fosters one big interoperable environment for decentralized ID.
The mission of DIF is to empower individuals and organizations by developing an open ecosystem for decentralized management of digital identities, championing secure, interoperable, and privacy-preserving technologies.
Practically, DIF has working groups that have contributed to key specifications such as Decentralized Identifiers and secure data exchange protocols.
For example, DIF contributors have worked on things like DIDComm, a secure communication protocol for sending data (like credentials or messages) between decentralized identity agents, and Decentralized Web Nodes (DWNs) for distributed data storage tied to DIDs.
DIF also coordinates with the World Wide Web Consortium (W3C) and other organizations on standards like the DID Core spec and Verifiable Credentials data model. The role of DIF in decentralized identity is somewhat analogous to what the Wi-Fi Alliance does for Wi-Fi – ensuring different devices and implementations can interoperate under common standards – except here it’s for digital identity.
Thanks to DIF’s work, a growing number of products and services (digital wallets, blockchain networks, authentication systems, etc.) speak the same language when it comes to decentralized identity. This collaboration is crucial for the future of digital identity: it means that your decentralized identity should work across borders and across different platforms.
In summary, DIF is helping to build the infrastructure of trust for decentralized identity, so that no matter who you are or where you are, you can use your decentralized credentials and DIDs seamlessly, just like we use email or web standards today.

Decentralized Digital Identity Benefits & Use Cases
Decentralized identity brings a host of benefits that address many of the weaknesses of traditional identity systems. With a decentralized identity system, users get enhanced privacy and control, and organizations benefit from stronger security and streamlined processes.
These advantages translate into a wide range of real-world applications across industries – from banking and finance to healthcare, travel, and even everyday online services. Let’s explore the key benefits (especially in terms of privacy, security, and user control) and then look at some concrete use cases showing how decentralized identity is being used today and what it enables.
Privacy, Security & User Control
One of the biggest benefits of decentralized identity is the improvement in privacy and security for individuals. Because you are not storing all your personal data in countless central databases, you dramatically reduce the risk of large-scale data breaches.
In a decentralized model, even if one of your credentials or accounts is compromised, it doesn’t automatically expose everything else about you. Each piece of data is compartmentalized under your control. Sensitive information is not concentrated in a single vulnerable location, which significantly reduces the risk of mass exposure.
For instance, if you use a decentralized ID to verify your age to a nightclub, that club doesn’t get to store your ID info in a database; they simply get a one-time cryptographic proof. There’s nothing valuable for hackers to steal from the verifier, and your most sensitive data stays with you.
In addition, decentralized identity often leverages advanced security techniques such as zero-knowledge proofs (ZKP) to enhance privacy. A zero-knowledge proof allows you to prove something about yourself without revealing the underlying data.
For example, with the right setup, you could prove “I am a citizen of X country” without exposing any other personal details or even your identity document number.
This concept is already being applied in cutting-edge solutions: Veridas’s ZeroData ID technology, for example, uses ZKPs to verify a user’s identity through their biometrics without storing any personal biometric data. It converts a person’s biometric (like a selfie) into an irreversible encrypted vector and embeds it in a QR code.
Scanning that QR code can confirm the person’s identity without ever revealing or saving the original face image, thus ensuring privacy by design. This level of privacy protection is virtually impossible in traditional systems where showing an ID means handing over all the info on it.
Security is also enhanced because authentication becomes cryptographic – instead of weak passwords or easily stolen personal details, you authenticate with possession of private keys and cryptographically signed credentials, which are far harder for attackers to compromise.
Closely tied to privacy and security is user control, sometimes referred to as self-sovereign identity. Decentralized identity empowers users to be the ones in charge of their identity data, rather than passive subjects of data collected by others.
You decide what information to share, who gets to see it, and you can often even set conditions (for example, a credential that expires or can be revoked by you). This flips the power balance: users feel less powerless about their personal information and more in control.
With an identity wallet on your phone, it’s like having your driver’s license, passport, work ID, and credit cards in your own pocket digitally – and only you can unlock and use them, typically via biometric or PIN authentication on your device.
This user-centric design also improves convenience. No more managing dozens of usernames and passwords or filling out the same forms for every new service – you can re-use your verifiable credentials to quickly sign up or log in to new services with confidence.
Many solutions offer a biometric login using decentralized ID: you just scan a QR or tap a button to present a secure credential instead of typing a password. That’s both easier for users and more secure (since phishing a cryptographic login is far harder than phishing a password).
Additionally, because all your credentials can be stored in one secure digital wallet, it streamlines the experience – just like having a single physical wallet, but for the digital world.
From a broader perspective, giving individuals control also builds trust: when users know they are only sharing what’s necessary and that they can withdraw consent, they’re more likely to engage with digital services without fear. Organizations, in turn, can demonstrate they respect privacy by adopting user-controlled identity processes, which can become a competitive advantage.
Overall, decentralized identity puts privacy, security, and user control at the forefront, solving many pain points of today’s identity systems (like data breaches, identity theft, and user frustration) by fundamentally redesigning how identity is managed.
Real-World Applications in Finance, Healthcare & More
The benefits of decentralized identity aren’t just theoretical – they are being realized in many real-world applications across various sectors.
In financial services, for example, banks and fintech companies are using decentralized identity for customer onboarding (KYC – Know Your Customer) and authentication.
Instead of making customers repeatedly submit the same identity documents to every bank or exchange (and each of those organizations storing copies of those documents), a customer can carry a “verified identity” credential in their digital wallet.
One bank (or a trusted identity provider) might issue a KYC credential after verifying the person once, and then other banks could instantly rely on that credential to onboard the customer, saving time and cost. This not only speeds up the process (opening a new account can go from days to minutes) but also reduces fraud, since the credential is tamper-proof.
Payment companies are also exploring decentralized ID to fight identity theft and credit card fraud – for instance, requiring a cryptographic proof of identity tied to transactions for an extra layer of security. In the EU, there’s a major push towards a unified digital identity wallet for citizens.
A large consortium backed by the European Commission (the WE BUILD project) is piloting an EU Digital Identity Wallet to cover use cases in payments, government services, and more, with nearly 200 partners involved.
Companies like Veridas are contributing their wallet technology to enable things like secure age verification for purchases and confirming senior citizen discounts via one-time identity proofs.
This shows how finance, government, and tech are coming together to use decentralized ID for everyday conveniences (buying age-restricted products, proving eligibility for benefits) in a privacy-preserving way.
In healthcare, decentralized identity can revolutionize how we manage health records and credentials. Consider vaccination certificates or COVID test results as verifiable credentials – instead of paper cards or PDFs (which can be forged or lost), patients could have digitally signed health credentials from hospitals or labs in their identity wallet.
When checking in for a flight or entering an event, they could present a proof of vaccination that is instantly verified as authentic, without exposing other medical details. Similarly, healthcare professionals (doctors, nurses) could have verifiable credentials for their licenses and qualifications.
A hospital onboarding a new doctor could quickly verify their credentials issued by a medical board, without lengthy background checks, by scanning a QR code or verifying a digital credential. This improves trust and safety in healthcare interactions.
Education is another area: universities are issuing digital diplomas as verifiable credentials, which graduates can share with employers globally. This cuts down on transcript fraud and makes resume verification much more efficient – a recruiter can validate a candidate’s degree in seconds rather than the slow process of sending requests to universities.
In the travel industry, decentralized identity could enable digital passports or traveler IDs that passengers control, potentially streamlining airport security and customs (with projects and trials already exploring this).
Enterprise and workforce use cases are also notable: companies can issue employee ID credentials for building access or VPN login, and when an employee leaves, those credentials can be revoked from their wallet – without worrying that copies exist elsewhere. It also means an employee could prove their past work history to future employers with credentials instead of references.
Even everyday scenarios like proving your age at a store, checking in to a hotel, or renting a car can be improved. Instead of handing over a physical ID (where someone might glance at all your personal info), you could flash a verifiable credential that only confirms the one thing needed (age, identity, or reservation details), protecting your privacy.
These real-world applications illustrate that decentralized identity isn’t just a niche tech concept; it’s actively solving problems: reducing onboarding friction, preventing identity fraud, enabling regulatory compliance (by providing auditable, signed evidence of checks), and giving users a smoother experience.
As a result, we’re seeing adoption in sectors like finance, healthcare, travel, government services, education, and enterprise IT – essentially anywhere identity verification is important. And this is just the beginning; the flexibility of the technology means new use cases are emerging rapidly, from managing IoT device identities to creating universal single sign-on across services using your decentralized ID.
The momentum suggests that many aspects of daily life that involve showing “ID” will be transformed by decentralized identity systems in the coming years.
Decentralized Identity Challenges & Future Outlook
As promising as decentralized identity is, it’s not without challenges. Being a relatively new paradigm, there are hurdles to overcome in technology, user experience, and policy before it fully realizes its potential.
However, the future of identity management is increasingly being shaped by this approach, with broad consensus that many current challenges can be addressed through ongoing innovation and collaboration. Let’s discuss some of the key challenges and then look at the future outlook of decentralized identity – why it’s expected to play a central role in the years to come.
The Future of Identity Management
Decentralized identity is an exciting and rapidly evolving concept, but achieving its vision requires tackling a few important challenges. One major challenge is user adoption and ease of use. Managing your own keys and credentials can be daunting for non-technical users.
If someone loses access to their identity wallet (for example, losing a phone without a backup), recovering those credentials or DIDs is not as straightforward as clicking “Reset Password” in a traditional system. The industry is actively working on solutions like social recovery (where trusted contacts help restore your identity) and backup mechanisms to make this safer. Another challenge is the need for a trusted ecosystem of issuers and verifiers.
For decentralized ID to work widely, many organizations need to issue verifiable credentials and many service providers need to accept them. This is a chicken-and-egg problem: verifiers want to see lots of users with credentials, and issuers want to know there are verifiers who will accept them. Initiatives like the DIF and government programs (e.g., the EU’s digital identity framework) are helping by standardizing technology and seeding initial use cases.
There’s also the question of interoperability: ensuring that a credential from one country or platform is recognized in another. This ties into setting global standards (which DIF and W3C are addressing) and establishing trust registries or networks (sometimes called “trust frameworks”) so that, say, a university in one country issuing a diploma credential will be trusted by employers in another country.
Privacy remains a double-edged sword challenge – while decentralized identity improves privacy, careful design is needed to prevent unintended data correlation. If not done right, using one identity everywhere could allow observers to link your activities. Techniques like having multiple DIDs and minimal disclosure credentials mitigate this, but they need to be consistently applied.
Lastly, regulatory and legal recognition is a hurdle: laws in various jurisdictions may need to catch up to recognize digital credentials and signatures as legally equivalent to physical IDs and paper. The good news is many governments are already moving in this direction, updating regulations to accommodate digital and decentralized IDs.
Looking ahead, the future of identity management is expected to be decentralized, user-centric, and highly interoperable. As technology keeps advancing and industries collaborate, we are likely to see big changes in how we manage and control our online identities.
The concept of self-sovereign identity – where individuals fully control their digital identity – is set to grow and become mainstream.
This will make online services easier to use (passwordless authentication, instant trust verification) and will allow different systems to work together seamlessly, because common standards will let identities roam across platforms. Governments are beginning to adopt digital IDs (for example, national ID programs that include digital wallets), and the next step is a broader push towards decentralized identity systems integrated into public services. We can expect more government-issued credentials (like driver’s licenses, passports, social security cards) to become available as verifiable credentials that people can hold in their personal wallets. A
s more governments take this route, businesses will feel the push to integrate these methods as well, creating a network effect. A country like Estonia – which has been a pioneer with its e-Residency and digital ID system – demonstrates how effective a digital-first (and somewhat decentralized) identity approach can be in providing secure, interoperable services. In the future, we might routinely use a single digital wallet to check into hotels, rent cars, prove our age, access medical records, and sign legal documents, all with cryptographic proofs rather than handing over raw data.
This promises stronger security (since every interaction is signed and verifiable), better privacy (since you only share what’s needed), and far more convenience.
The future identity ecosystem will likely involve lots of behind-the-scenes coordination – blockchain networks or other distributed systems might serve as the backbone for DIDs and credential registries, and standards ensure that whether you’re using a wallet from company A or service B, they all speak the same language.
We can also anticipate biometrics playing a role in simplifying user experience – for instance, using your voice or face (stored securely) to unlock your decentralized ID wallet and sign transactions, combining security with convenience.
In fact, solutions like biometric-bound decentralized IDs (e.g., the earlier mentioned ZeroData ID that ties a biometric vector RBR to your decentralized credential) hint at a future where you are the key to your identity in the literal sense.
Overall, the trajectory is clear: decentralized identity is poised to reshape digital life, making it safer and more user-friendly. As this technology matures and adoption grows, we’ll move closer to a world where identity verification is instant but private, and individuals truly own their digital identities – fulfilling the promise of the future of digital identity.
The path isn’t without obstacles, but with ongoing innovation and cooperation (through bodies like DIF and forward-thinking industry leaders), decentralized identity stands out as the foundation for the next generation of identity management. The future of identity is being built now, and it is decidedly decentralized.