Home / Solutions / Core / Biometric Check

Unlock the power of facial recognition technology with precise 1:1 identity validation and 1:N identification, ensuring accurate and secure identification in any scenario.





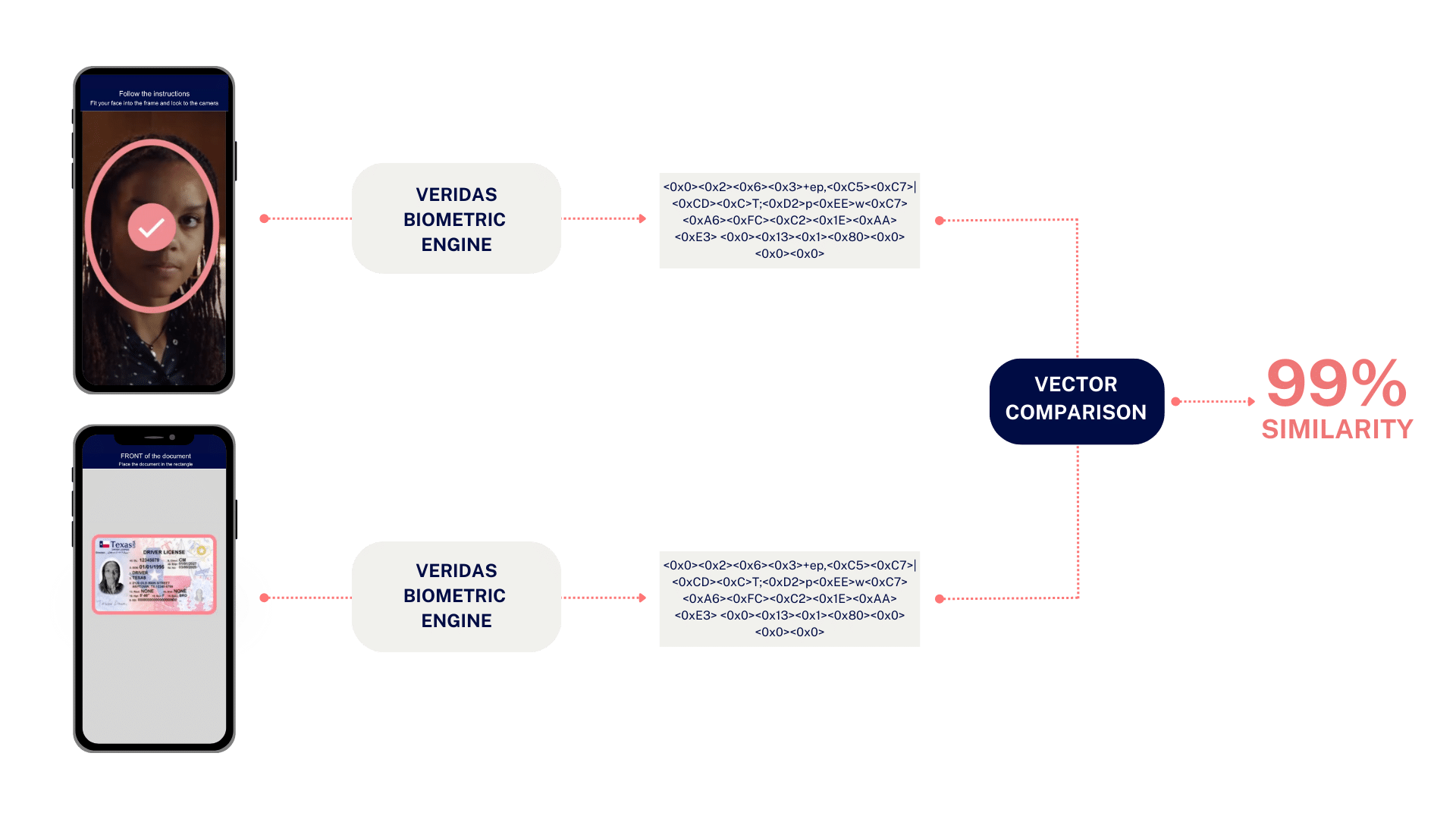
In a 1:1 identity verification process, facial recognition typically compares a live image of a person with another image of the same individual.
For instance, during an identity verification process, this ensures that the individual is the same as the one depicted in the identity document, confirming the document’s validity and the person’s identity.
At Veridas, we go beyond simple image comparison. We utilize our biometric engine to transform these images into biometric vectors—private, irreversible, and non-interoperable representations of an individual’s facial features. These biometric vectors are then compared to ensure a more secure and efficient authentication process.
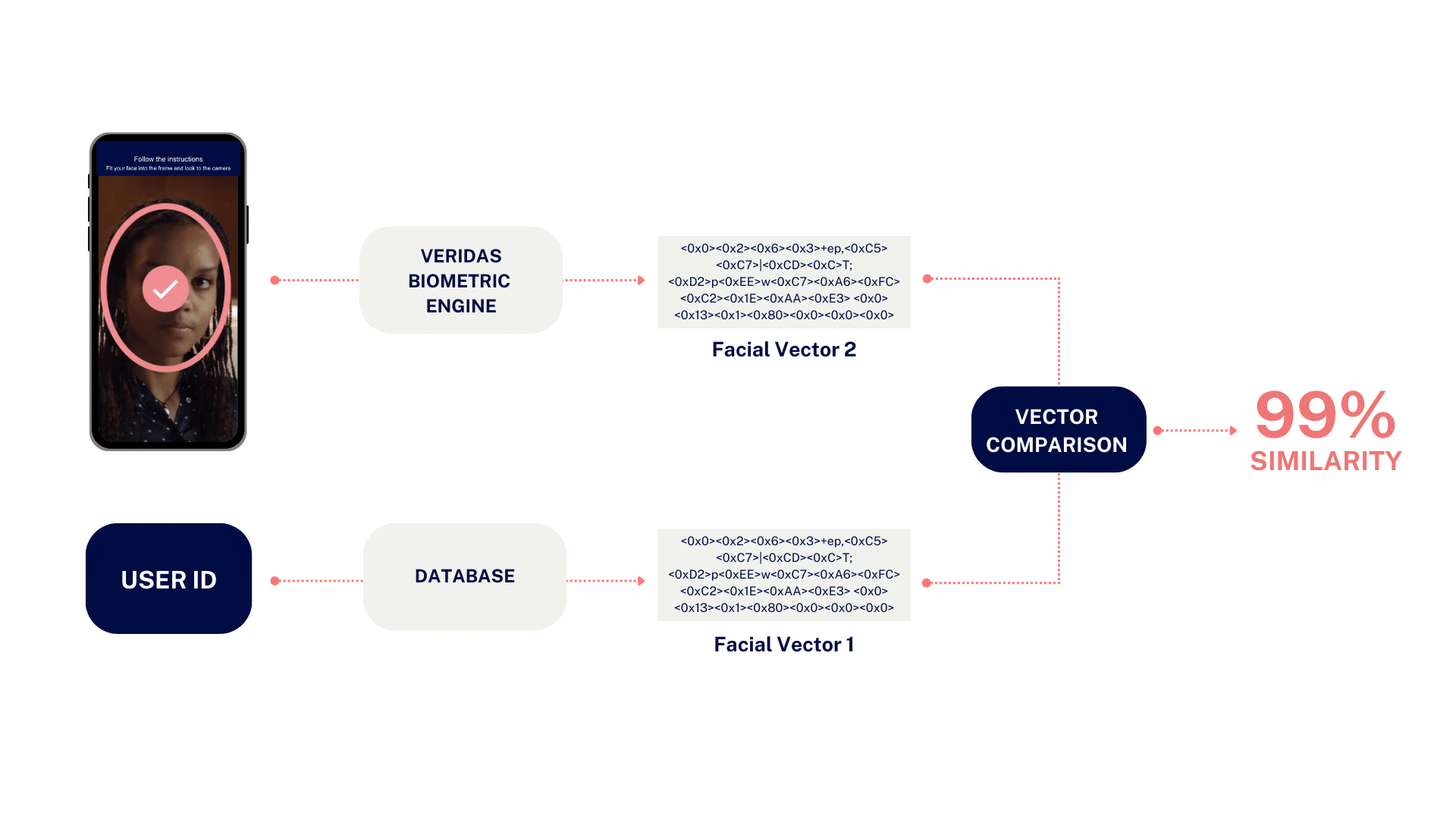
In a 1:1 authentication process, a unique identifier (such as an email address) is used to retrieve a specific reference image.
At Veridas, we elevate this process by transforming both the reference image and the user’s live image into biometric vectors using our biometric engine.
Next, the system compares these vectors, ensuring real-time authentication that confirms the individual’s identity without requiring a large database search.

The process starts by capturing a facial photograph from various sources—whether it’s a selfie taken during digital onboarding, an image from the client’s database, or one taken in person at a branch.
This image is sent to a biometric engine, which processes it to generate a facial vector—a private and anonymous mathematical representation of the person’s biometric features. The original facial image cannot be reconstructed from this vector. The facial vector is then stored for use in future biometric authentication processes.

The process begins by obtaining a new photograph of a person’s face, which is then processed by a biometric engine to generate a facial vector, representing unique facial features. This vector is used to retrieve the corresponding user identifier and the previously stored facial vector from a database.
The two vectors are compared, and the distance between them is normalized to determine their level of similarity. A high similarity score indicates a successful biometric match, while a low score suggests a failed match.
Access to a facial vector does not reveal the identity of the individual. The vector alone cannot identify the person it represents.
Each facial vector is encrypted with a distinct key, varying by version, model, and client.
The system maintains consistent accuracy across all age, gender, and racial groups
Facial vectors can be revoked and updated if a vector database is compromised, ensuring ongoing security.
Facial vectors do not reveal or allow inference of personal details such as health status, mood, or gender.
Facial vectors are purpose-specific and cannot be repurposed for different uses. Each vector is uniquely tied to its biometric model and intended application.
Facial vectors generated by AI-based biometric models cannot be converted back into the original raw data, ensuring the vector remains both irreversible and private.
1:1 facial recognition verifies identity by comparing a live image with a specific reference image to confirm if they belong to the same person. In contrast, 1:N recognition identifies an individual by comparing a facial image against multiple images in a database to find the closest match.
Facial vectors generated by biometric technology are private and anonymous. It is not possible to reconstruct the original image from these vectors, and they are encrypted with unique keys, ensuring irreversibility and identity protection.
No, each biometric vector is uniquely generated for a specific use case and cannot be repurposed for other applications, reinforcing data security and privacy. These vectors are private, irreversible, and non-interoperable.
If a security breach is detected, biometric vectors can be revoked and updated to maintain the integrity and security of the system.
No, the facial recognition technology described is accurate and unbiased across all age, gender, and race groups, ensuring fair and consistent results.

/Let’s talk!
Become part of our network and add the best verification solution on the market to your product catalog.
Simplify entry, save time, and manage your stadium parking more efficiently.
Enter the parking area in under 1 second with facial recognition technology.
Simplify the ticket purchase process and enable attendees to enjoy a hands-free experience throughout their stadium stay.
Elevate your parking security for peace of mind.
Protect your Stadium with our end-to-end identity verification platform, featuring biometric and document verification, trusted data sources, and fraud detection.
Verify your attendees’ identity remotely in less than 1 minute.
Simplify the ticket purchase process and enable attendees to enjoy a hands-free experience throughout their stadium stay.
Enhance the security of the purchase process, eliminating the possibility of fraud, resale, and unauthorized access.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.