What does biometric mean?
According to ISO 2382-37, biometrics is “the automatic recognition of individuals on the basis of their biological and behavioural characteristics”.
Biometric recognition is based on physical, physiological or behavioural characteristics (biometric characteristics). Since its inception, a multitude of systems have been developed, using more and more types of biometric features, while at the same time expanding the use cases to which they can be applied.
Today, biometrics based on physical characteristics of the individual are arguably the most widespread, developed and therefore mature. Among the most widely used biometrics are facial biometrics, voice biometrics, iris biometrics and fingerprint biometrics.
In contrast, it is important to stress what biometrics is NOT.
- Biometrics is not the characterisation of an individual on the basis of gender, race, sexual orientation, religion or political beliefs.
- Nor is biometrics the analysis of a person’s state of mind. It is not the detection of emotions or the study of human reaction to different stimuli.
- Biometrics is not the identification of a person’s state of health or physical condition. It does not identify diseases, nor physical parameters such as pulse, blood oxygen or blood pressure. Nor does biometry determine a person’s predisposition to disease. The above points are dealt with by technical disciplines other than biometrics.
Biometric technology can be applied in two different ways:
- Identification (1:N). This is the method known as 1:N, since it compares an individual against a group (i.e. against each of the persons in that group).
The aim is to find out whether that individual is one of those belonging to that group. It should also be borne in mind here that it is not the same (and this is precisely the basis for the distinction made in the forthcoming European AI regulation) whether this identification is carried out with the user’s knowledge and consent, or “remotely” (i.e. without that knowledge).
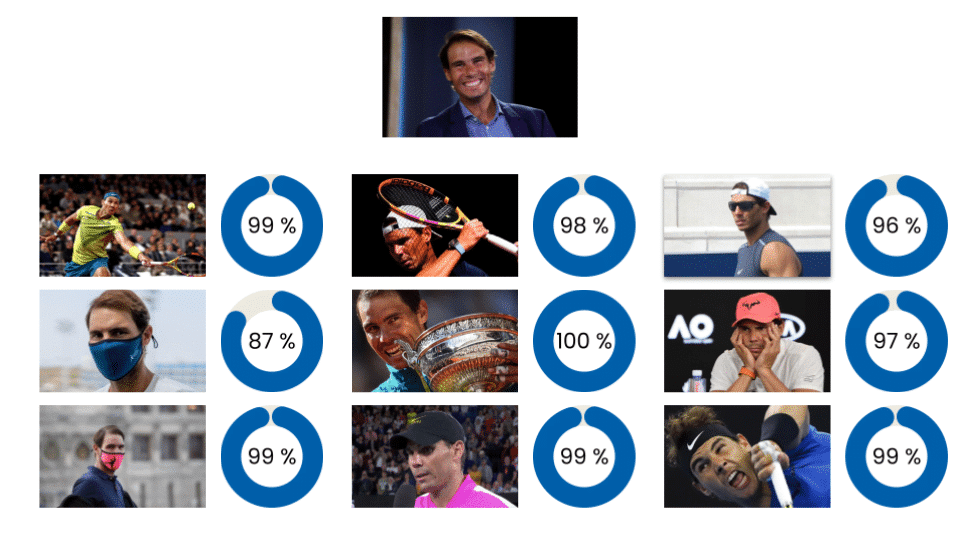
The following example shows a 1:N search using an image of Rafa Nadal and identifying his face in a database of photographs of the tennis player in different scenarios.
- Authentication or verification. This method is based on a 1:1 comparison, as the individual’s data is compared against other data associated with that same individual. The purpose in this case is to verify his or her identity, i.e. to verify that he or she is who he or she claims to be.

- Identification (1:N). This is the method known as 1:N, since it compares an individual against a group (i.e. against each of the persons in that group).
What is biometric authentication?
It can be said that the key element in a biometric recognition system is the engine used. A biometric engine is understood as the set of mathematical processing implemented in a computer system that allows the recognition of a person based on one or more physiological characteristics.
Two stages are usually defined in all biometric processing.
- Biometric enrolment.
- Biometric matching. The biometric matching process can have two purposes: verification (1:1) or identification (1:N), as described above.
The functioning of each of the steps is explained below.
Biometric registration
Biometric enrolment consists of the generation of a biometric vector from a physiological characteristic of the person. For example, from the face, voice, fingerprint, iris, etc. The following image shows an explanation of the enrolment process for the specific case where the face is used as a biometric factor. In this case, the biometric vector is referred to as face vector.
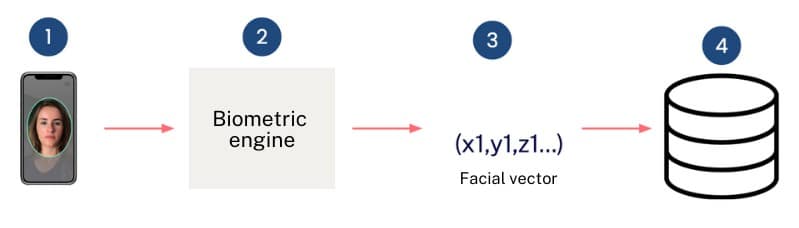
- The first step consists of obtaining a photograph containing the person’s face.
- This image is sent to the biometric engine, which carries out the image processing. This is the most important step, since depending on the technologies used, the biometric engine will be more or less accurate. Later sections detail the evolution of biometric engines from models based on landmarks to current models based on Artificial Intelligence.
- As a result, the biometric engine obtains a face vector, referenced as (x1, y1, z1…) in the above scheme. The face vector is a mathematical representation of the biometric characteristics of the person.
- As a result of the enrolment process, the face vector is stored so that it can be used in a subsequent biometric comparison process. The face vector is stored in association with a person identifier. This identifier can be a fully anonymised value (e.g. a hash obtained from the person’s name or ID number).
This storage can be in a centralised database, distributed or even stored on the user’s mobile device.
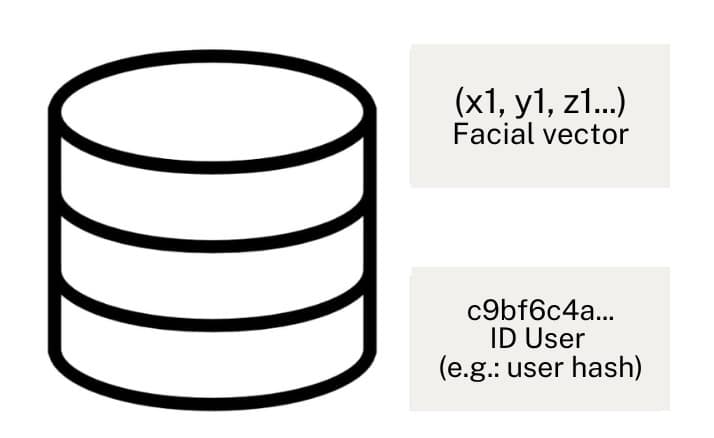
Biometric comparison
The biometric matching process consists of generating a new face vector from a new capture of the person’s physiological characteristic, and comparing it to the previously stored face vector.
From a technical point of view, it is important to note that it is not pixel-by-pixel images that are being compared, but facial vectors.
The following image shows an explanation of the process for the specific case where the face is used as a biometric factor.
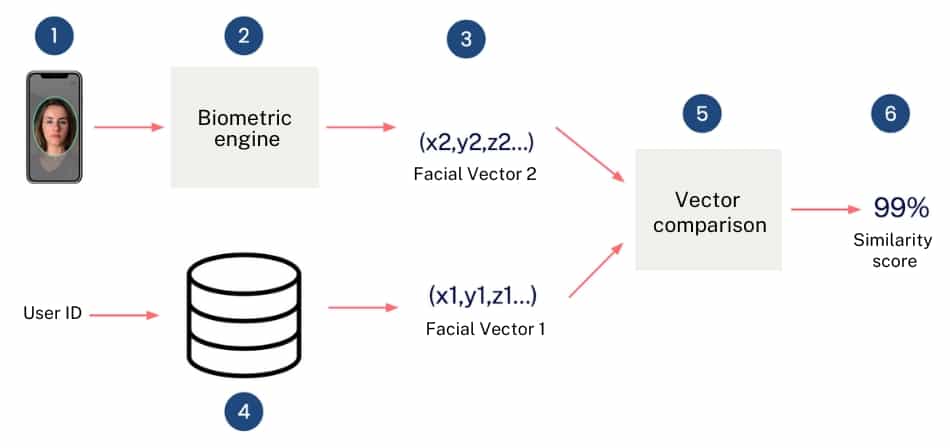
- The first step consists of obtaining a new photograph containing the person’s face.
- This image is sent to the biometric engine, which carries out the image processing.
- As a result, the biometric engine obtains a face vector referenced as (x2, y2, z2…) in the above scheme.
- The user identifier associated to the vector is obtained. This allows finding in the database the previously stored face vector, referenced as (x1, y1, z1…) in the previous scheme.
- Subsequently, a comparison between the two previous vectors is carried out. The vector matching process does not involve the use of advanced technology. From a mathematical point of view, the cosine rule is usually used to determine how far apart the two vectors are.
- Finally, the distance between vectors obtained in the previous point is normalised to represent the level of similarity between the compared vectors. In this way, vectors that are close to each other will obtain a high level of similarity. That is, they represent situations where the biometric comparison is successful. On the contrary, vectors that are far apart will obtain a low level of similarity. That is, they represent situations where the biometric comparison is not successful.
Evolution of biometric engines
To understand the above, it is necessary to distinguish between two types of biometric engine models.
- Old-school or minutiae biometric models.
- AI-based biometric models.
In both scenarios, a face vector is obtained from the biometric characteristic of a person, as explained above for the enrolment and matching processes, although the characteristics of this vector are totally different in terms of security, accuracy and privacy.
Modern AI-based biometric engines are 100 times more accurate than minutiae-based engines. They are also more accurate than people carrying out the facial recognition process. While the probability of error is not zero, the accuracy values achieved can exceed 99.999% accuracy, as will be discussed below.
Additionally, AI-based biometric engines have led to advances in terms of ensuring data protection and user privacy. Leading-edge biometric technologies that have reached the so-called “state of the art” have basic characteristics per se that make them private by design.
Biometric minutiae or “old-school” models
Old-school’ biometric engines were the most widespread until 2017 and are based on ‘landmarks’ or characteristic points to recognise, for example, a face.
This method involves taking measurements between multiple biometric feature points, such as a facial image. This is where the name bio-metrics comes from.

However, this type of modelling may entail a risk for data protection, since a person with the necessary knowledge of the system may be able to interpret the measurements represented by the characteristic points of the subject’s face (e.g. being a facial image: the distance between the eyes, between the ears, etc.), and thus obtain an estimate of the original image. And therefore, with this information, it might be possible to reconstruct the original image and identify the subject.
Moreover, these systems are mostly standardised, which means that their operation can be known by anyone (e.g. through the standard defined by ISO 19.785 – Information Technology Common Biometric Exchange Formats Framework).
While this makes these technologies interoperable (such as fingerprint recognition systems), it has security implications. An attacker who has access to the face vector generated by an “old-school” system could try to use that face vector for authentication in a different system that is interoperable with the first one. To mitigate this risk, the face vector can be encrypted.
Modern AI-based biometric models
The General Data Protection Regulation (EU Regulation 2016/679) sets out in Article 25 the principles of data protection by design and by default.
These principles seek to ensure that, taking into account the state of the art, the costs and the nature, scope, context and purposes of the processing, and the risks that may arise, the most appropriate technical and organisational measures are implemented to ensure data protection principles and to protect the rights of data subjects.
This can take many forms, but biometric recognition undoubtedly refers to the use of advanced and state-of-the-art technologies that provide a high level of protection, i.e. the “state of the art” technology in this field.
Additionally, data protection must be taken into consideration in the design of AI-based biometric engines, so that they incorporate technological elements that provide a sufficient guarantee for privacy.
Companies developing state-of-the-art technology have moved away from “old-school” models to models based on Artificial Intelligence and, more specifically, neural networks. The NIST, in the USA, evaluates the quality of the same, in November 2023, 539 algorithms evaluated.
Facial vectors generated with Artificial Intelligence have the following characteristics.
- Private: It is not possible to know who the vector represents simply by having access to it.
- Irreversible: It is not possible to retrieve the photo of the person from an AI-generated face vector.
- Non-interoperable: It is not possible to use a face vector generated by one manufacturer in the biometric engine of another manufacturer. Additionally, the face vector generated by one biometric model is incompatible with another version of the biometric model, even from the same manufacturer. Face vectors generated for one client and use case are also incompatible with vectors generated for another client.
- Encryption: The vector is encrypted with a unique key for each version, model and client.
- Revocable: It is possible to cancel and update the face vector in case a vector database is compromised.
- It does not include additional information about the person (health status, mood, gender, etc.) and does not allow inferences to be made about these characteristics.
The following sections elaborate on the characteristics of AI-based face vectors.
There are independent international bodies that evaluate biometric systems. NIST (National Institute of Standards and Technology) is a federal agency within the US Department of Commerce. NIST’s mission is to promote innovation and industrial competitiveness by advancing standards in ways that improve economic security and quality of life.
It is the international benchmark for evaluating and classifying biometric engines. The presence in this classification serves to compare the performance of the biometric engine in different categories.
In the field of facial biometrics, the report of 21 November 2023 (see report) shows the evaluation of 539 biometric engines from 337 manufacturers, where it is estimated that almost all the systems evaluated are based on Artificial Intelligence.
The accuracy levels achieved with a model using Artificial Intelligence are much higher than those obtained by a landmark-based biometric system. For example, the evaluation of the best landmark-based biometric models obtain an accuracy of 95% in the LFW database while AI-based systems obtain accuracies above 99% and use other more complex databases to assess their accuracy (see evaluation).
Biometric authentication: technical explanation
In the following, the operation of AI-based biometric engines for vector generation is explained, with particular reference to the case of facial biometrics.
- Obtaining a photograph of the person, containing the face.
- Detection of the face in the previous image, and extraction of the face of interest, usually by cropping a segment of the image obtained in the previous point.
- Normalisation of this to a lower resolution image (100×100 pixels, for example). At this stage, transformations can be applied to the image to improve its frontality and thus reduce the variability due to the specific context of the capture.
- Processing of the previous image in a neural network. The internal processing of the neural network consists of a composition of non-linear functions that transform the image at each step of the algorithm. For example, an architecture known as ResNet101 could be used. This would have 101 components or processing stages. At each stage of the algorithm, the dimensionality of the image is reduced until it is transformed into a mathematical vector.
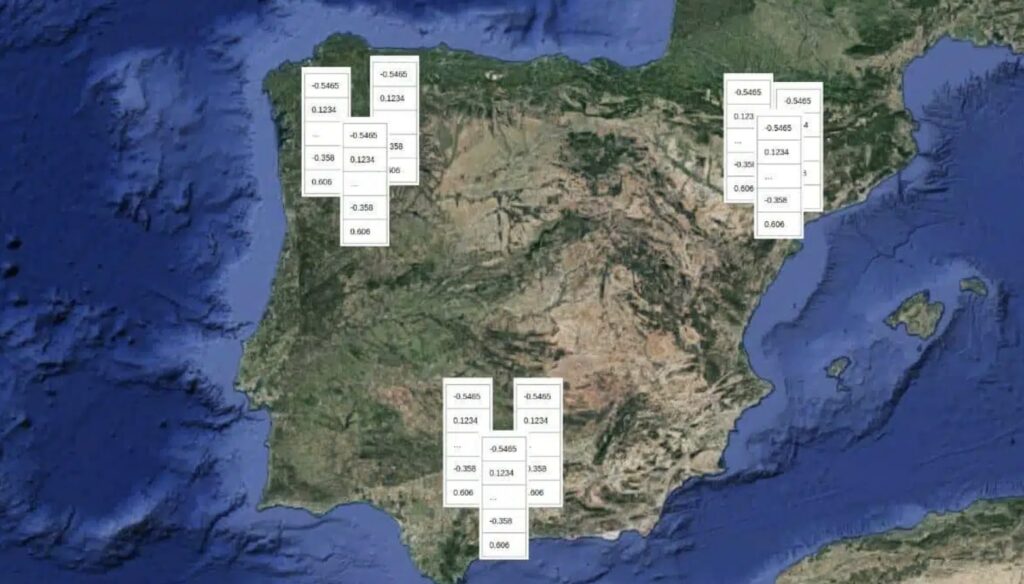
This vector typically has 512 components. That is, just as traditional physical space is defined by 3-dimensional vectors (x, y, z, or latitude, longitude and altitude), the space in which the face vector is defined has 512 dimensions.
As in physical space, the face vector indicates a specific direction in space. The specific direction in space is unique for each person.
A visual representation of this idea can be seen in the following image. In this example, images less than 100 km away belong to the same person. On the other hand, images more than 100 km away belong to different people. The closer the images are to each other, the more confidence there is that they belong to the same person.

It is important to note that in order to compare the similarity between two people it is not necessary to store the images. In this example, the images are used as a visual resource, but the most correct visualisation is actually the one in which only facial vectors are compared.
What is a biometric proof of identity?
It is important to note that the security of the biometric proof of identity is increased if the capture of the biometric characteristic is controlled.
In facial biometrics, this refers to the taking of a selfie-like photograph at the very moment when the user carries out an enrolment and verification process.
When the capture is integrated into the process, it ensures that the user cannot provide previously taken or even manipulated samples. It is also ensured that the person does not use a photograph available on social networks, or synthetically generated through generative Artificial Intelligence.
Additionally, the capture can be complemented with a request for an active action by the individual. This allows for a confirmation of the person’s willingness to perform this process (e.g. by asking them to move their head, this prevents the selfie from being taken automatically without their knowledge).
In relation to international standards, ISO 29.794-5 Information Technology-Biometric sample quality aims to define and specify methodologies for the calculation of objective and quantitative quality scores for facial images.
On the other hand, ISO 19.794-5 Information technology – Biometric data interchange formats specifies an enrolment format for storing, recording and transmitting the information of one or more facial images or a short video stream, as well as constraints, properties, attributes and best practices of facial images.
In any case, AI-based facial biometrics technologies can perform biometric matching on images that do not comply with the requirements of the above ISOs.
What are the main types of biometrics?
The assessment and choice of the type of biometric system to be used (facial recognition, voice, fingerprint, etc.) must be made for each case of use, taking into account its particularities. And, in particular, it must take into account the ease of the means of capture, as well as accessibility by all groups.
- For example, facial biometrics requires the use of a camera to capture the data, which can be a mobile phone, tablet, computer or any other type of camera integrated with the system.
- Voice biometrics, on the other hand, requires a microphone to record the audio, whether from a mobile device, computer, etc.
- For fingerprint biometrics, a high-resolution sensor or camera is required to read the fingerprint; this sensor can be embedded in a device, as is the case with mobile phones.
The choice of the biometric or set of biometric data used determines the accessibility and scope of the identification system. A facial biometric system is accessible to virtually all individuals, regardless of potential health problems or physical characteristics (e.g. scars), whether temporary or permanent.
Voice biometrics systems are also accessible to a very high percentage of people, with the sole exception of those with hearing or vocal sensory impairments that prevent them from expressing themselves orally.
When the systems are based on fingerprints, they can also be used by a large number of people, the majority of the population, but it must be taken into account that some illnesses and the performance of certain professions or manual jobs deteriorate the fingerprint data, making them difficult to recognise.
In any case, in terms of accessibility, any capture system should adhere to the WCAG 2.2 guidelines and aim to comply with level AA (see reference), as well as Directive (EU) 2016/2102 on the accessibility of websites and mobile applications of public sector bodies (see reference).
How does biometric authentication work?
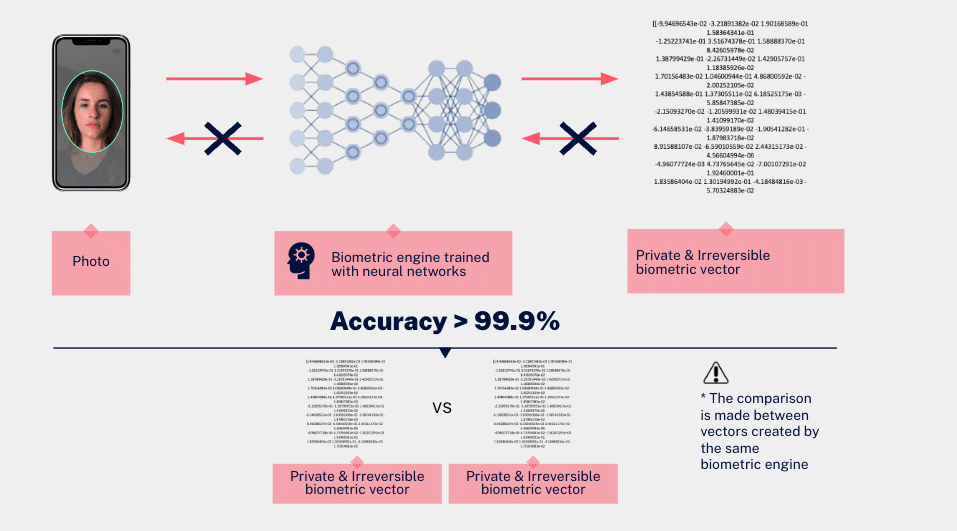
In recent years, biometric engines have been developed with Artificial Intelligence. These systems are trained to recognize faces like the human brain, distinguishing a person in different circumstances plus greater precision due to the infinity of data they can process.
Biometric engines are designed to protect the privacy of their users by default. When a facial image or an audio fragment is processed, this evidence is converted into an irreversible mathematical vector. If that vector got lost or someone tried to read it, it would be impossible.
It can only be compared with another vector (a new image or audio at the time of verifying a person’s identity).
Furthermore, these vectors can only be processed by the same engine that created them. This means they are interoperable since other systems cannot use them. These requirements are reflected in the Guide of the Spanish Data Protection Agency (AEPD) as essential for the use of biometric systems.
What are the purposes of biometrics?
Biometrics allows us to verify our identity in the digital world safely and accurately. The European Union’s payment services directive (PSD2) defines three levels of security or ways in which we can verify our identity:
- Possession (something you have): This is the most traditional way of accessing a service that belongs to us. It is through a key or physical accreditation. This would be the case of the key to our house, our car, or even our identity document. The significant risk of this means of authentication is the possibility of losing this credential or that someone impersonates us simply because they can steal it
- Knowledge (something you know): If we advance a little, at a level above, we will find what we know, for example, a password or access code. In this case, it is not something physical that we can lose. Still, there is a risk that we forget it or even that another person finds out that information by different methods, impersonating us.
- Inherence (Something that you are): Above the previous ones, and as the authentic means of verification, we find ourselves and everything that makes us unique. In the same way that it would seem ridiculous to call our parents and give them a code to recognize us, it is archaic that today, in the digital age, we are still slaves of passwords and physical credentials to prove our identity. Biometrics allows us to verify our identity in a simple, fast, and available way on any occasion, either through a selfie or by saying a few words.
Veridas, just be you
Veridas has been in the world of biometrics-based Artificial Intelligence for four years, developing its own facial and voice recognition engines. Our globally recognized technologies are already in operation in different banking, insurance, or telecommunications sectors. Millions of identities have been verified worldwide in an agile, fast, and secure way since then.
Our mission is to protect the identity of people in the digital world and fight against online fraud, ensuring that digitization has a social impact by improving the quality of people’s lives. Thanks to Veridas, you can forget about passwords, face-to-face red tape, endless calls in call centers, or identity theft… just be you.