Introduction: technology and regulation hand in hand thanks to Veridas
Spain can be considered a pioneer in the regulation of digital verification processes of citizens’ identities. This is a fact. It was already a pioneer several years ago, along with some other European Union countries, such as Germany, and it is still a pioneer today.
Ever since human beings started doing business with each other, being able to trust the other party in a relationship has been the cornerstone of that relationship. And that trust starts with knowing who that person is, to know whether the operation we are carrying out with him or her involves greater or lesser risk, or simply to be able to determine whether it is possible to carry out that operation.
This has always been so obvious to us, but it becomes even more important when these operations are carried out at a distance, with people we did not know beforehand. Confidence that the other party is who they say they are is even more fundamental, as we cannot rely solely on our knowledge and instincts, but need to rely on other tools to make decisions.
The great development of digital identity verification tools in recent years has meant that, in processes that require a high level of security in the identity of the people with whom we interact, these specific technologies are required to be incorporated.
Identity verification for money laundering prevention
In Spain, the Executive Service of the Commission for the Prevention of Money Laundering and Monetary Offenses (SEPBLAC), belonging to the Bank of Spain, was among the first institutions in the world to authorize, already in 2016, remote identification for the initiation of transactions with regulated entities, such as the opening of current accounts in banks.
Article 21.1.d) of the Regulation of Law 10/2010, of April 28, provides that regulated entities may establish business relations or execute transactions by telephone, electronic or telematic means with customers who are not physically present when the customer’s identity is accredited through the use of secure customer identification procedures in non-face-to-face transactions, provided that such procedures have been previously authorized by SEPBLAC.
The first milestone is the authorization of non-face-to-face identification
Thus, in February 2016, SEPBLAC published the “Authorization of non-face-to-face identification procedures through videoconferencing”, which states that “Technological innovation in the financial sector has the potential to reduce costs, increase competition and provide a better service to customers. Consequently, it is advisable to favor the use of new technologies as long as they provide adequate levels of security”. It goes on to list the characteristics that tools must have to achieve this adequate level of security, among which the following stand out:
- “Implement the technical requirements that ensure the authenticity, validity, and integrity of the identification documents used and the correspondence of the holder with the client being identified.
- Full recording of the videoconference held between the client and an operator with specific training, “with a record of date and time”.
- The customer being identified must visibly display the front and back of the document used for identification.
- Keep, in addition to the recording, a “photograph or snapshot of the front and back of the identification document used” that meets the “conditions of quality and sharpness that allow its use in investigations or analysis.”
From assisted verification to automated video-identification
A year later, in May 2017, SEPBLAC considered that “The promotion of technological innovation in the financial sector now makes it advisable to also authorize video-identification procedures in which there is no online interaction between the potential customer and an agent or operator of the obliged subject (unassisted processes)”, and published its “Authorization of video-identification procedures”. Some requirements are equivalent to those required for the previous process, while others are now added to provide additional safeguards and enhance the process through videoconferencing:
- Implement the technical requirements to verify the authenticity, validity, and integrity of the identification documents used and the correspondence of the holder of the document with the client being video-identified.
- Perform the process from a “single device” and with “live” transmission of images and sound (i.e. no pre-recorded files are allowed).
- Recording of the video identification, “with a reliable record of its date and time”, to allow its later reproduction.
- “In the course of the video-identification process, the client must visibly display the front and back of the document used for identification.”
- Keep, in addition to the recording, “a photograph or snapshot of the front and back of the identification document used” that meets the “conditions of quality and sharpness that allow its use in investigations or analysis”. As a novelty, SEPBLAC expressly indicates that for these purposes “the mere capture of stills of the video-identification process” will not be considered valid; that is to say, it is required that in addition to a video recording, a photograph of the front and back of the document be captured separately. Since this is an assessment to ensure the security and preservation of evidence, it is understood that this limitation should also apply when a video conferencing process is used.
- The subsequent review of all evidence of the process by a specifically trained operator.
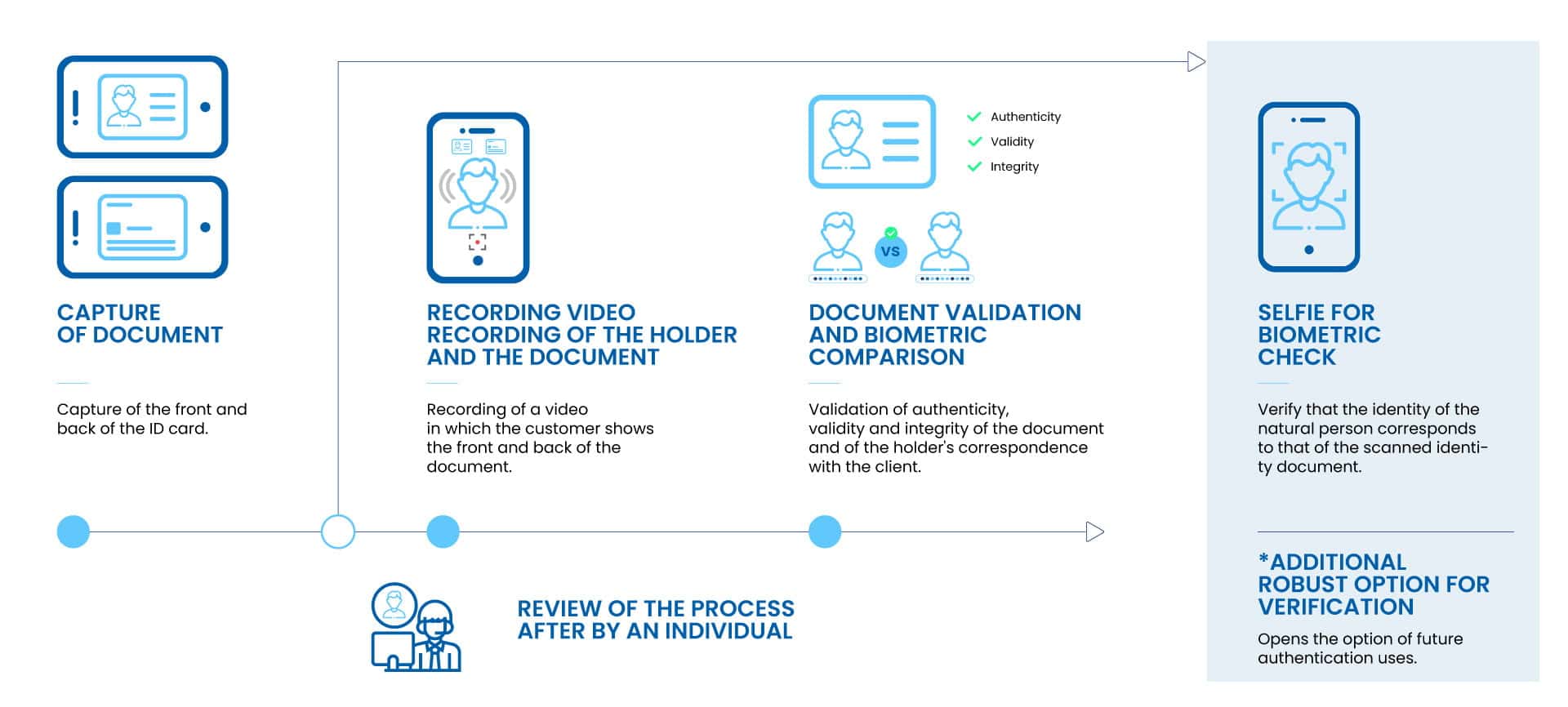
How can a non-face-to-face identity verification process be carried out in banks and other regulated entities?
The following chart shows how a non-face-to-face identity verification process should look like according to SEPBLAC.
Identity verification for trusted e-services
Experience in the banking sector has led to the adoption of a digital identity verification system for the issuance of qualified electronic certificates.
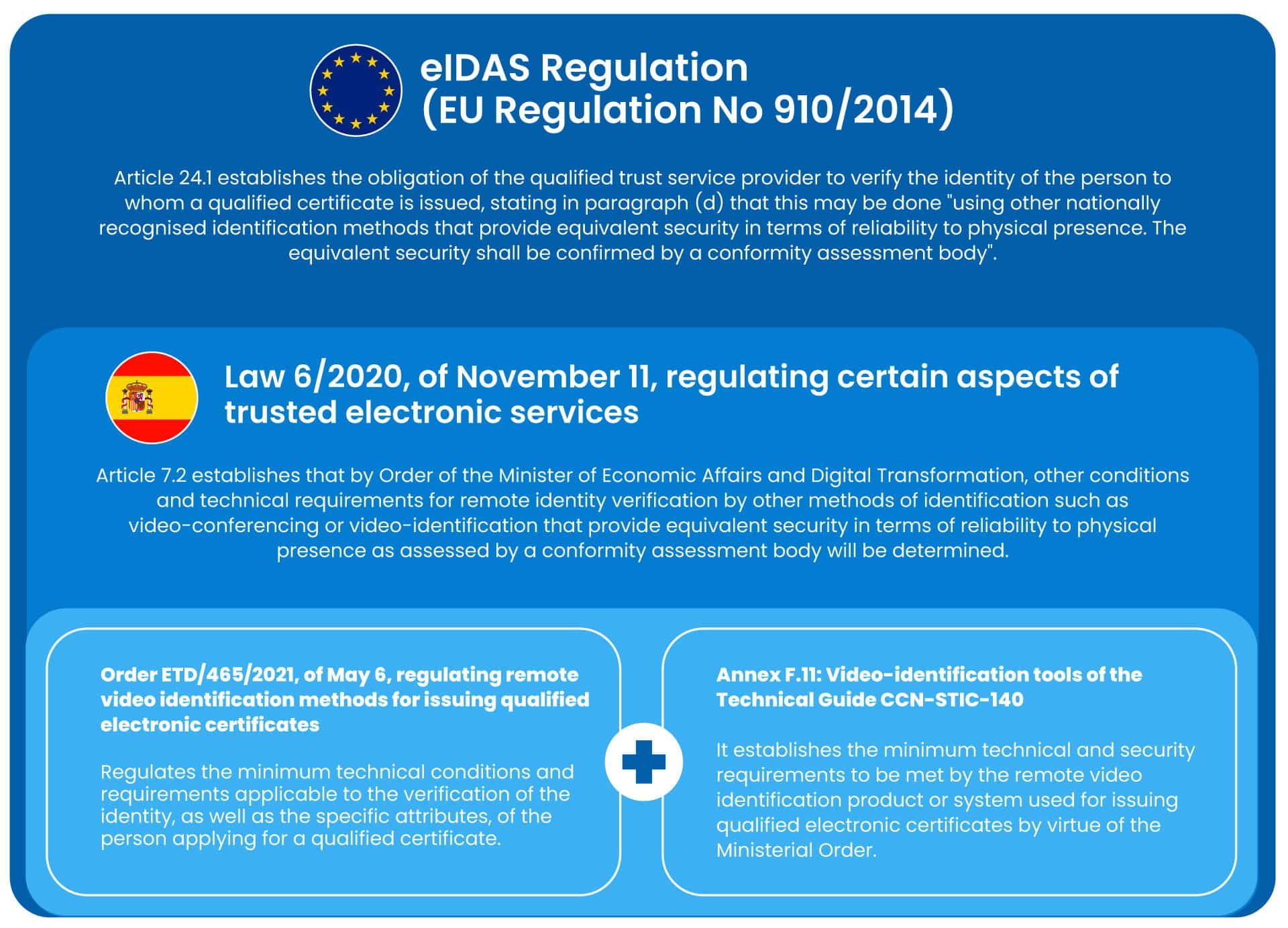
Article 24.1.d) of Regulation (EU) No. 910/2014 of the European Parliament and of the Council of 23 July 2014 on electronic identification and trust services for electronic transactions in the internal market and repealing Directive 1999/93/EC states the following:
“24.1. When issuing a qualified certificate for a trust service, a qualified trust service provider shall verify, by appropriate means and in accordance with national law, the identity and, if applicable, any specific attributes of the natural or legal person to whom the qualified certificate is issued.
The information referred to in the first subparagraph shall be verified by the qualified trust service provider either directly or by relying on a third party in accordance with national law: (…)
(d) by using other identification methods recognised at national level which provide equivalent assurance in terms of reliability to physical presence. The equivalent assurance shall be confirmed by a conformity assessment body.”
After the approval of provisional measures during the first state of alarm derived from the health crisis in Spain and whose validity was limited to that period, in November 2020 Law 6/2020, of November 11, regulating certain aspects of electronic trust services was approved, whose article 7.2 states that:
“2. By regulation, by Order of the person holding the Ministry of Economic Affairs and Digital Transformation, other conditions and technical requirements for remote identity verification and, if applicable, other specific attributes of the person requesting a qualified certificate shall be determined by other identification methods such as videoconferencing or video-identification that provide equivalent security in terms of reliability to physical presence as assessed by a conformity assessment body. The determination of these conditions and technical requirements will be made based on the standards that, where appropriate, have been determined at the Community level.
For the provisions of this paragraph, nationally recognized identification methods shall be considered to be those that provide equivalent security in terms of reliability to physical presence and whose equivalence in security level is certified by a conformity assessment body, by the provisions of the regulations on trusted electronic services”.
This regulation was materialized in Order ETD/465/2021, of May 6, regulating remote video identification methods for the issuance of qualified electronic certificates, and at a technical level is complemented by Annex F.11 on Video identification tools of the ICT Security Guide CCN-STIC-140. Thus, qualified trust service providers wishing to issue qualified certificates verifying the identity of the applicant remotely, must comply with Order ETD/465/2021 and use a certified tool according to the guide CCN-STIC-140-Annex F.11.
A process is thus established that must comply, among others, with the following requirements:
- Guarantee that the process is executed in the unity of action, so that it can be evidenced that it is a single process in a single device and a single sequential act in time, regardless of whether it is executed in several steps (GEN.1).
- Real-time execution, obtaining the evidence during the process, not allowing pre-recorded files (GEN.2).
- To verify the authenticity, validity, and integrity of the identity document, the tool must be able to perform a series of specific controls (DOC.1 to DOC.6 and DOC.9).
- Verify the correspondence of the document holder with the certificate applicant, using facial recognition technologies that have been evaluated by NIST reaching a certain level of accuracy (SOL.2).
- Verify that the applicant is a live person and implement presentation attack detection mechanisms (SOL.3).
- Recording of a video (or a video call) in which the applicant shows the front and back of his/her document (requirement derived from Order ETD/465/2021).
- A subsequent review of all evidence of the process by a specifically trained operator (SOL.1, DOC.7, and DOC.8).

The need for an appropriate European regulation
Also noteworthy is the recent publication of ETSI Technical Specification TS 119 461, which contains a standardization of the identity verification process.
ETSI is a European standardization body responsible for the regional standardization of telecommunications, broadcasting, and other electronic communications networks and services. It has a key role in Europe that includes supporting European regulation and legislation through the creation of harmonized European standards.
Although the process described above is currently operating in Spain, it is interesting to point out the provisions of ETSI TS 119 461, which may be applicable in other European Union countries or, after regulatory reform, in Spain.
In this sense, ETSI establishes different requirements depending on whether the identity verification is performed in person or remotely, the latter being assisted or unassisted.
For the remote identity verification process, the following requirements, among others, apply:
- Employ an identity document containing a printed photo (COL-8.2.3-02).
- Use an identity document in its original form (COL-8.2.3-05). In other words, it is not possible to use a photocopy of the document.
- Establish a series of security measures if the process requires the reading of the identity document chip, to ensure that the content read from the chip is authentic and has not been injected (VAL-8.3.2.04).
- The verification process must include a video showing the user showing both sides of the document (VAL-8.3.3.3-04). It is important to consider that the standard establishes that the exclusive use of a photograph of the document is not sufficient, but in no case does it establish the impossibility of using photographs.
- It requires the use of biometric algorithms systematically evaluated against reference databases. An example of this type of evaluation is performed by NIST FRVT, as indicated by ETSI (BIN-8.4.3-07).
It establishes the need to use life testing techniques by ISO/IEC 30.107-3 (BIN-8.4.2-06). This requirement goes beyond that requested by SEPBLAC and by Order ETD/465/2021.





![[DEMO GRATUITA]: Descubre cómo funciona nuestra tecnología en vivo](https://no-cache.hubspot.com/cta/default/19918211/478bcde8-f23d-4436-a640-ce15a25d0877.png)