From the user’s image or voice, we create an irreversible biometric vector, ensuring that the original image can never be reconstructed.

The user takes a selfie, undergoes an IDV process, or records an audio.

Our biometric engine, trained with neural networks, transforms this data into a private, irreversible, and non-interoperable biometric vector.

We encrypt the biometric vector along with relevant contextual data (e.g., ticket purchase, employee ID) into a secure QR code, creating a unique identification document linked to the user’s biometric characteristics.

Our biometric QR code empowers advanced authentication methods with the best user experience to provide unparalleled access to both physical and digital services.
It is not possible to know whom the vector represents simply by having access to it.
The biometric vector is encrypted with a unique key for each version, model, and client.
It is not possible to retrieve the photo of the person from a biometric vector generated by Artificial Intelligence.
Each biometric vector is uniquely generated for each biometric model and each use case.
The vector generated from the user's photo contains no sensitive information, so its loss poses no risk to either the user or the client.
It is possible to cancel and update the biometric vector in case a vector database is compromised.
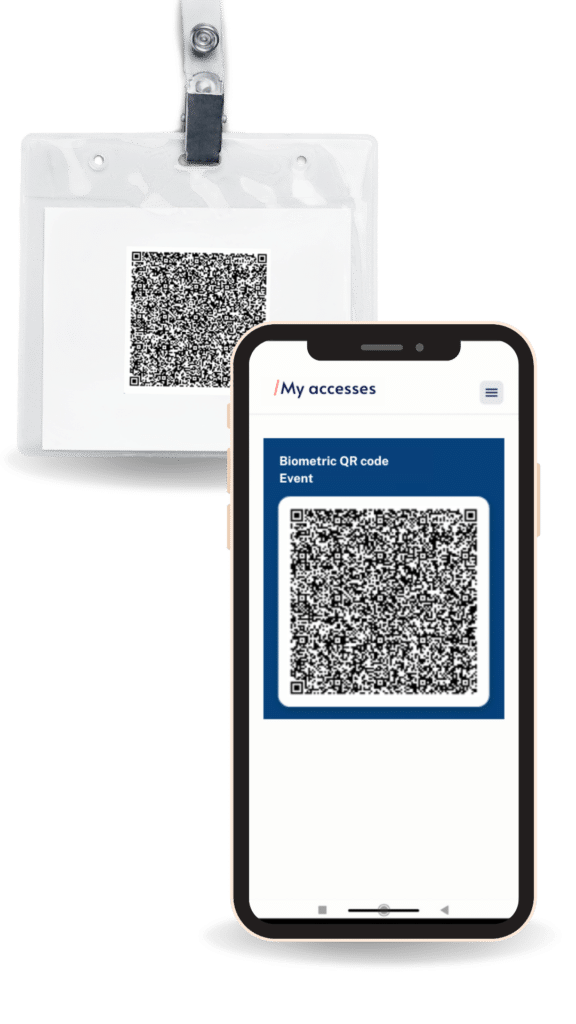
The biometric QR can be stored on the user's device, within an app, in an email, wallet, badge or printed on paper.
The biometric QR can be configured to expire after a defined time period, adding an additional layer of security and flexibility to access control policies.
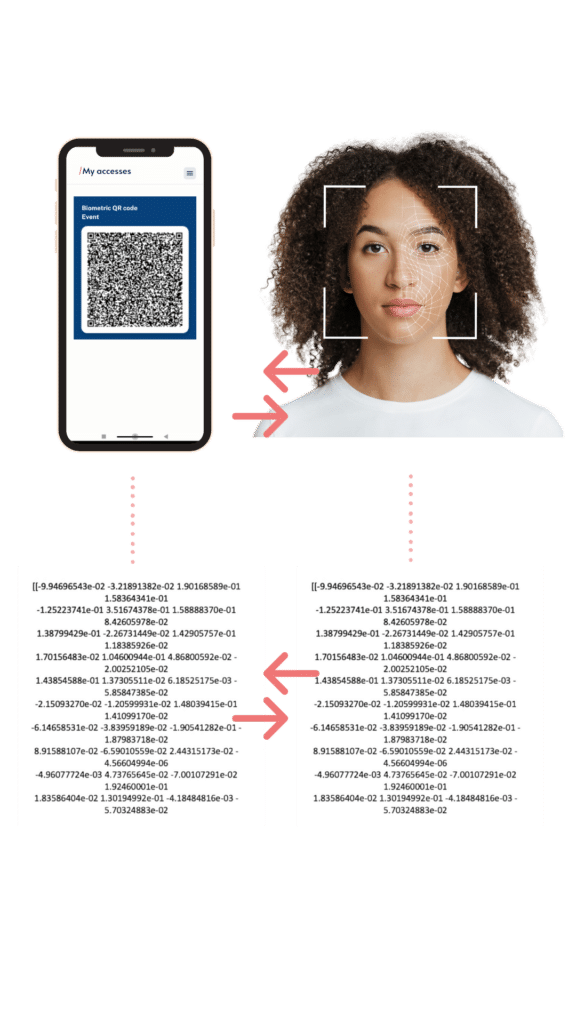

The user scans the biometric QR code using a compatible device such as a facial reader, smartphone, or computer. Upon scanning, the biometric QR code is decrypted and its contents are extracted.

Veridas captures the user’s image and transforms in real-time it into a biometric vector, which is compared with the biometric vector stored within the QR code.

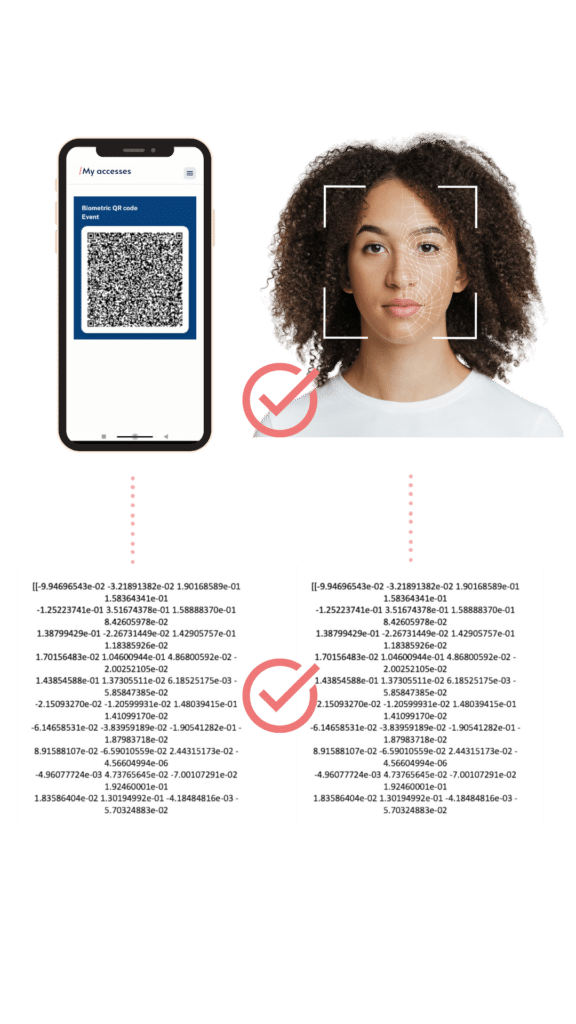
The device performs a 1:1 comparison to make a match. If the biometric data matches the stored biometric vector and the contextual information is validated, the user gains access to the desired service, location, or transaction.
Veridas doesn’t retain any information during credential generation or verification, minimizing the risk of breaches. All necessary data for identity verification is contained within the credential, enhancing security and compliance.
Users maintain absolute control over their biometric data, as Veridas does not store any of it. This approach not only improves privacy but also ensures compliance with data protection regulations, thereby fostering trust in the authentication process.
By seamlessly integrating biometric authentication with QR codes, users can effortlessly authenticate themselves for both online and offline services, streamlining access control processes.
We are pioneers in the development of this patented technology, so we have exclusivity in the use of this system worldwide.
Secure all your entries and exits.
A secure and private solution.
Streamline registration, control access and collect valuable data.
Enhancing the efficiency and reliability of authentication processes.
Enhance security and prevent fraud in digital banking.
/Success Stories

Simplify entry, save time, and manage your stadium parking more efficiently.
Enter the parking area in under 1 second with facial recognition technology.
Simplify the ticket purchase process and enable attendees to enjoy a hands-free experience throughout their stadium stay.
Elevate your parking security for peace of mind.
Protect your Stadium with our end-to-end identity verification platform, featuring biometric and document verification, trusted data sources, and fraud detection.
Verify your attendees’ identity remotely in less than 1 minute.
Simplify the ticket purchase process and enable attendees to enjoy a hands-free experience throughout their stadium stay.
Enhance the security of the purchase process, eliminating the possibility of fraud, resale, and unauthorized access.