Veridas has become the first company in Spain to successfully pass the qualification tests required by the new National Cryptologic Center (CCN) guidelines for its Digital Onboarding solution.
This critical achievement will allow those Qualified Trust Service Providers (QTSPs) that use Veridas technology to comply with the regulation required for issuing qualified digital certificates.
This requirement will come into force from March 1, 2023. It will be mandatory for any QTSP that wants to continue operating in Spanish territory and wishes to perform identity verification before issuing qualified certificates in a non-presential way. And, for the moment, only Veridas has a qualified solution for this purpose.
What is the CCN Security Guide, and why is it important?
To understand the role played by the CCN Security Guide in issuing qualified electronic certificates, it is necessary to go back to 2014, in the context of the regulations approved by the European Parliament.
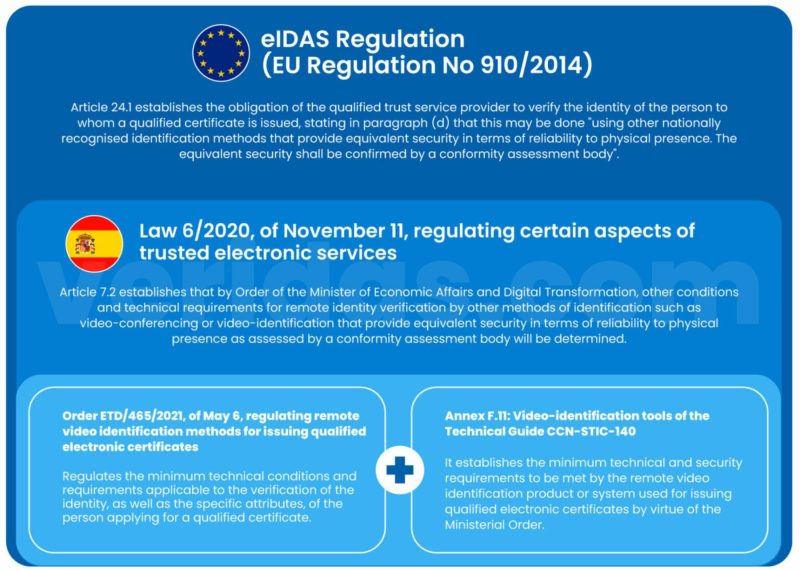
Through the eIDAS regulation (regulation no. 910/2014), concerning electronic identification and trust services for electronic transactions in the internal market, the European Parliament opens the door for issuers of qualified electronic certificates to use for the verification of the identity of applicants “other identification methods recognised at national level which provide equivalent assurance in terms of reliability to physical presence. The equivalent assurance shall be confirmed by a conformity assessment body” (Article 24.1.d)
More recently, in 2020, Spain passed Law 6/2020, dated November 11, to regulate certain aspects of electronic trust services. In this law, reference is made to a new order where “other conditions and technical requirements for remote identity verification and, if applicable, other specific attributes of the person requesting a qualified certificate will be determined by other identification methods such as videoconferencing or video-identification that provide equivalent security in terms of reliability to physical presence as assessed by a conformity assessment body” (Article 7.2)
This order, ETD/465/2021, was finally approved on May 6, 2021, and it regulates remote video identification methods for issuing qualified electronic certificates. But on a technical level, and this is where the National Cryptologic Center comes into play, it was complemented by Annex F.11 on Video identification tools of the TIC Security Guide CCN-STIC-140.
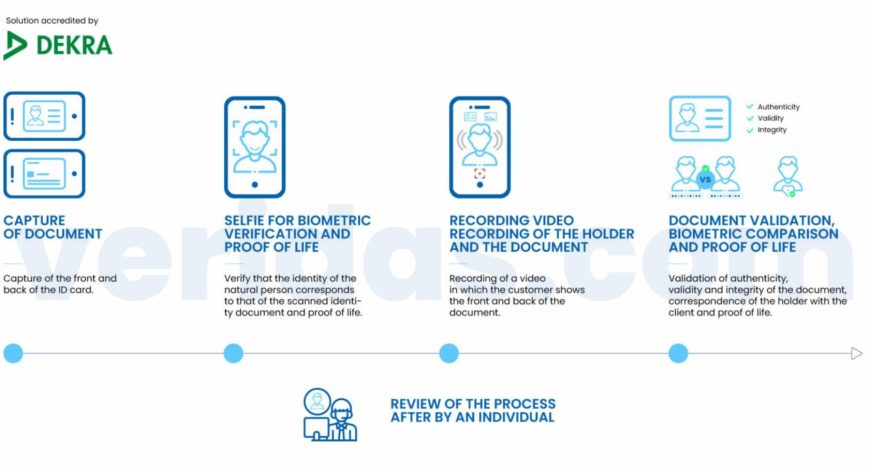
This first version of the annex has recently undergone modifications, making it much more demanding in its technical requirements. Veridas has passed the tests carried out by DEKRA, one of the world’s leading organizations in the TIC sector (Testing, Inspection, Certification), both for the previous version and the new version of Annex F.11 of March 2022, a prerequisite for qualification by the CCN.
What are the requirements of the new version of CCN Annex F.11?
Annex F.11, as last amended in March 2022, distinguishes between Fundamental Security Requirements (RFS in its Spanish acronym) – which includes reference to the assessment of the Biometric Evaluation Module (MEB in its Spanish acronym) -, validation of submitted documents and optional Fundamental Security Requirements. Veridas has been evaluated by DEKRA against all requirements of the CCN guide, satisfactorily passing all the tests performed.
It is essential to highlight that the product has been the subject of 70 document fraud attacks and 230 facial biometrics attacks in the mobile web environment. The product had to guarantee the automatic detection of 100% of the cases without considering human intervention. These tests have meant overcoming one of the most demanding environments developed by an evaluator to date.
CERTIFICATION AND EVALUATION REQUIREMENTS
In this section, where reference is made to the required certifications and evaluations, it is worth mentioning how the CCN demands all qualified solutions to have their biometric engines evaluated by the National Institute of Standards and Technology, NIST, considered the most prestigious independent evaluator body in the world. Veridas has always submitted its facial and voice biometric engines for evaluation by the NIST, obtaining fantastic results yearly.
Specifically, the guide requests that “the biometric facial matching system between the applicant and the ID photo must have been evaluated, according to the Face Recognition Vendor Test (FRVT) in the VISABORDER category, by NIST and have obtained an FNR (False Negative Rate) of less than or equal to 5% for a FPR (False Positive Rate) of less than or equal to 1/1,000,000. The database used for the test must be the one used by NIST in 2020 or higher” (Article 24).
In this regard, Veridas obtained an FNR rate of 0.80% in its last submission in September 2021, well below the rate required by the CCN, which places it among the best biometric engines worldwide.
FUNDAMENTAL SECURITY REQUIREMENTS (RFS)
- Protection against evidence capture attacks: the tool must ensure that a single device is used in a single sequential act of time. In addition, it must ensure that the process is executed in real-time without allowing pre-recorded files.
- Biometric verification: the tool should provide facial biometric verification through the captured selfie and document. It should also incorporate active or passive liveness detection and implement presentation attack detection (PAD) mechanisms.
To assess the biometric verification requirements, the CCN specifies that the evaluator should do this by applying IT-14, also known as the biometric evaluation module (MEB). These requirements are explained later in the article. - Auditing: the annex defines different characteristics that the auditing tool accompanying the manufacturer’s solution must have.
- Secure communications: the tool must establish secure channels when exchanging sensitive information with authorized entities or between different parts of the product, following the guide CCN-STIC-807.
- Trusted administration: the tool shall ensure that only a user with administrator permissions can perform administrative functions, distinguishing between the role of configurator and auditor.
- Identification and authentication: the tool shall identify and authenticate each user before granting access, implementing mechanisms to prevent attacks, protecting the confidentiality and integrity of authentication credentials, and blocking or close the session after a certain period of inactivity.
- Protection of credentials and sensitive data: if the tool stores credentials and/or other sensitive data, these should be stored using the cryptological mechanisms authorized in CCN-STIC-807.
VALIDATION OF SUBMITTED DOCUMENTS
This section of Annex F.11 details the following requirements regarding the validation of submitted identity documents:
- The tool shall implement detection mechanisms for replay attacks and print attacks.
- The tool shall be able to verify that the validity date of the document has not expired.
- The tool shall check the data integrity of the Visual Inspection Zone (VIZ) with the Machine Readable Zone (MRZ).
- The tool shall generate alerts to the operator whenever it detects any of the described attacks or failed test checks.
BIOMETRIC EVALUATION MODULE (MEB)
As mentioned above, the MEB establishes a set of tests to be performed by the laboratory on the software under evaluation (Target Of Evaluation or TOE) to verify the biometric verification capability of the tool under assessment. In this set of tests, six types of attacks to be prevented are distinguished:
- Imposter presentation attacks: this test aims to verify that the TOE is not vulnerable to the impersonation of a bona fide user by an attacker resembling the bona fide user.
- Presentation attacks using videos: this test aims to check that the TOE is not vulnerable to the impersonation of a bona fide user by an attacker using a video of a bona fide user.
- Presentation attacks using very low-cost masks: this test aims to verify that the TOE is not vulnerable to an attacker’s impersonation of a bona fide user using a low-cost (e.g., paper) mask as an artifact.
- Presentation attacks using advanced masks: the objective of this test is to verify that the TOE is not vulnerable to the impersonation of a bona fide user by an attacker using an advanced mask as an artifact.
- Presentation attacks using makeup: this test aims to verify that the TOE is not vulnerable to the impersonation of a bona fide user by an attacker using makeup as an artifact.
- Attacks using deepfake computing tools: this test aims to verify that the TOE is not vulnerable to an attacker’s impersonation of a bona fide user using deepfake tools. These tools can manipulate video and sound, superimposing such those elements on the actual images. Focusing on a possible use of identity theft, deepfakes would be used to modify the face of one person on the video where another person appears.
What does having a CCN-qualified solution allow me to do?
To date, Veridas Digital Onboarding is the only solution available on the market that will enable a QTSP to issue qualified electronic certificates in a non-face-to-face manner as of March 1, 2023.
This recognizes Veridas’ continued work towards the qualification and ongoing assessment of all its solutions, seeking to provide a high degree of certainty to its customers and setting the industry standard for independent evaluations.
Veridas certifies compliance with all relevant regulations in all sectors in which it operates, such as anti-money laundering regulations (AML), data protection regulations (GDPR or CCPA), or the different standards in information security (ISO 27001 and ENS) or the one that regulates liveness detection (ISO 30.107) where we have recently obtained level 2 by iBeta.
Veridas uses 100% proprietary and fully automated technology (no human in the loop), which allows it to achieve very high levels of accuracy without compromising privacy and security.
In addition, the commitment to a Phygital approach to the identity challenge allows our customers to cover all their needs under a single provider: from digital onboarding of new customers to their authentication in both digital and physical environments.




![[FREE DEMO]: Verify the identity of your users in 1 minute. The digital onboarding solution that is revolutionizing the market.](https://no-cache.hubspot.com/cta/default/19918211/4cd17904-6ed7-4f6f-85cc-7a829106743d.png)
![[DEMO GRATUITA]: Descubre cómo funciona nuestra tecnología en vivo](https://no-cache.hubspot.com/cta/default/19918211/478bcde8-f23d-4436-a640-ce15a25d0877.png)















